The Cabinet Office Technology Transformation programme was established to replace an end-of-life outsourced IT service.
The aim of the programme is to enable modern flexible ways of working and to provide civil servants with technology at least as good as they have at home.
During user testing at the start of this project, staff told us that they wanted better connectivity; greater choice of applications; to be able to be more mobile with more portable devices and to be able to collaborate on documents in real time.
Architecture design
When designing the architecture for a service that would enable all of those things, we made a decision early on to start with a ‘green fields’ approach.
Whilst we did have legacy architecture and data to deal with, we wanted to be clear that this wouldn’t constrain our new design in any way. This gave us the freedom to genuinely consider any technical solution or product, and it’s become an approach that’s baked into our decision-making now. We first choose the best thing for the users and then worry about the details - like how to secure it, or how to procure it.
The introduction of the new Government Security Classifications around the time of our early design work was fortuitous in allowing us to properly consider commodity cloud services, some of which might not have been possible under the old security regime.
The architecture we have now is far from being ‘finished’ and it never will be! We’ll continue to constantly evolve as new or better products and services come along.
Choose your own device
One very clear output of our user research was that there is no “one-size-fits-all” solution when it comes to devices.
In most cases this was down to different needs: some users work almost entirely on documents and email, whereas others process heavy data-driven applications. Some need big screens that they view throughout the day; others spend much of their time travelling or moving between meetings. For some users, it’s less about “need” than about preference - but we feel this is not something we should ignore; IT doesn’t always know best.
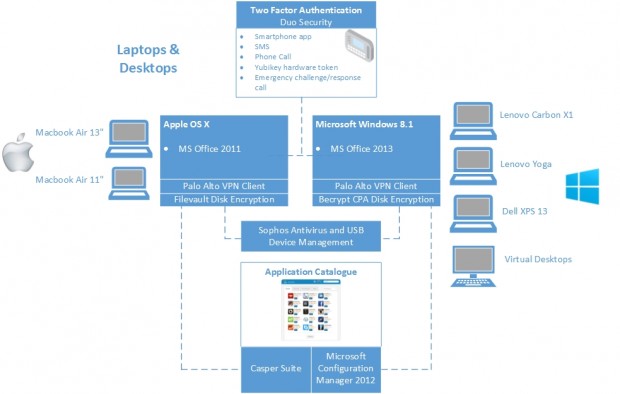
We needed to balance the need for device options against the costs and capacity to manage diverse devices, and to do this we offered users a choice of device from five options. Today this includes two sizes of Apple Macbook Air, a Dell XPS 13, a Lenovo Carbon X1 and a Lenovo Yoga. So far we’ve found that there is roughly a 50/50 split in choice of device between Mac and Windows laptops.
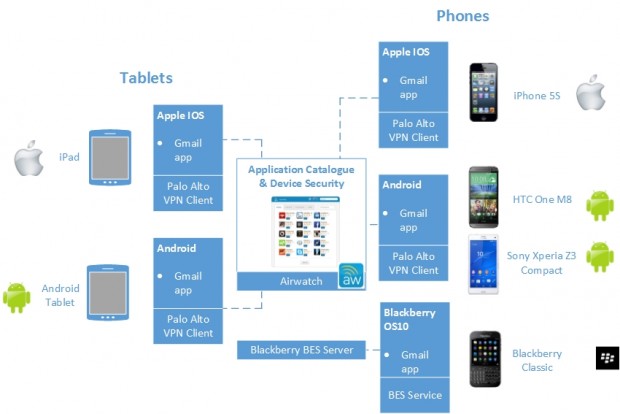
We have a similar catalogue of smartphones with a mixture of Apple IOS and Android phones and are about to launch some tablet options.
This device choice decision was not taken lightly. We carefully considered the increase in software and support required to maintain both Windows and OSX devices and discovered it was minimal, and worth the additional effort.
Always On VPN
From the outset we had a vision to make the service safe for OFFICIAL use and to simultaneously make the user experience as seamless as possible. One key point of this was to maintain the user experience regardless of location. Whether a user is sitting in a government building or at their local coffee shop, the system should ‘just work’.
To achieve this, all devices have a Palo Alto VPN client which is always connected and, importantly, connects without user input. This means a user can open their laptop and immediately start working safely, but also that all traffic transits our core network - so we can filter, monitor and log all useage from all of our devices.
Laptops
All our laptops, phones and tablets are managed according to the CESG End User Device guidance. We’ve found this to be pragmatic advice and we’ve had no problems implementing it without adversely affecting the user experience.
We use a combination of products and services to achieve this:
- Microsoft System Center Configuration Manager to manage Windows, and the JAMF Casper suite for OSX.
- Cloud-based services like Google Apps for Work are protected by using two-factor authentication services and federated identity services. In practice, this means that users need to log in through a portal page which we manage, so they never know their own passwords for Google Apps and they are unable to access the services from an uncontrolled device.
- All computers have a balanced security policy applied - users are able to change cosmetic features like wallpaper and look and feel, but they cannot install their own software. Instead, we have provided a self-service download application with only approved, secure and licenced software.
Mobiles and Tablets
Mobiles and tablets are managed in a similar way to laptops, however here we use the Airwatch Mobile Device Management suite to enforce the policies recommended by the CESG End User Device guidance.
Devices are configured so that users cannot install apps from regular app stores. Instead, we have deployed a Cabinet Office app store containing pre-approved apps for IOS and Android.
Today we have around 20 apps available in the store, including commonly used things like news and productivity apps. We continuously add to the offerings in the app stores based on user requests.
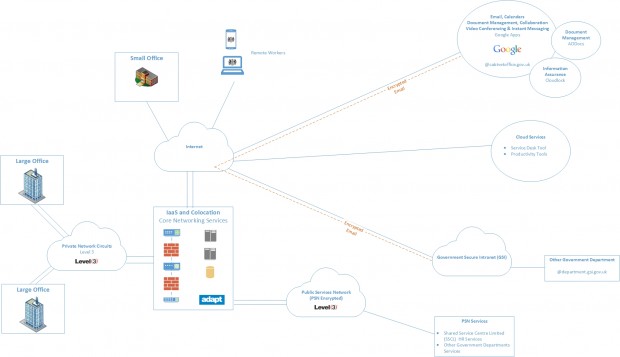
Core infrastructure
Our core infrastructure was designed to provide a lightweight ‘wrapper’ to add the assurance we need for OFFICIAL to the the public cloud services we use. It’s also where we operate our device management services, identity services and logging and monitoring.
In line with the Cloud First policy, the goal here was to minimise the amount of physical infrastructure we bought and instead to use commodity cloud services where possible.
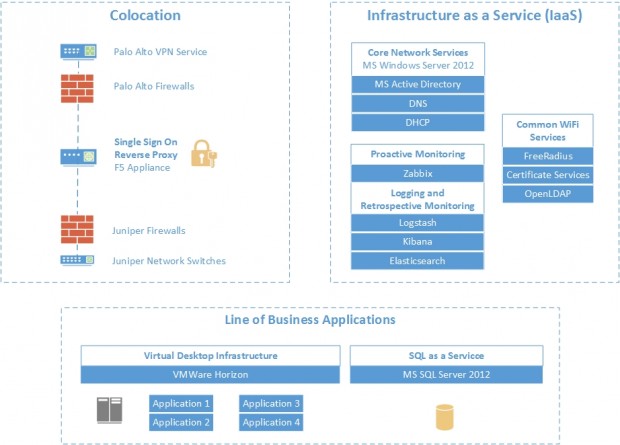
We use Infrastructure as a Service (IaaS) from a G-Cloud supplier called Adapt. This IaaS service provides on demand compute and storage capacity as well as other managed services like SQL as a Service. It is provided on a flexible monthly billing cycle, allowing us to increase or decrease capacity as required.
A small range of vendors are used for our core networking components including Palo Alto, Juniper and F5. Collectively these products provide us with firewall services, VPN termination, Single Sign On, Intrusion Prevention and application reverse proxying.
After exploring options for identity management, including open source options like OpenLDAP, we decided on Active Directory for user accounts.
We use an open source product called Zabbix for Infrastructure monitoring, logging and alerting.
I’m happy to say that all of the physical network equipment for the three departments we support fits into less than half a rack of space!
Building services
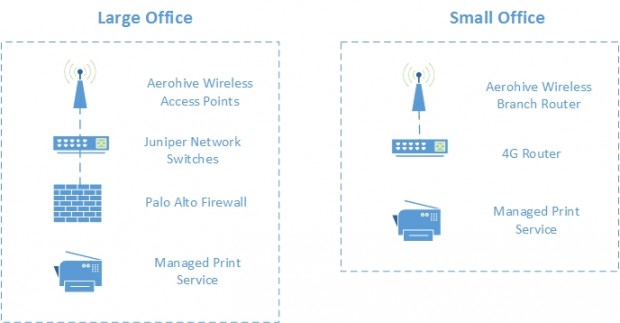
Our user research told us that users did not want to be tied to an ethernet cable on a desk, so our approach to building networking can be summarised as ‘WiFi everywhere’.
Because of our ‘always on VPN’ architecture, we were able to achieve this very cost- effectively. Since the security is ‘built in’ to the client devices, we didn’t need to go to extreme lengths to secure the WiFi itself in buildings. We are, however, continuing to develop a WiFi architecture pattern which will ensure that government laptops can connect to a trusted WiFi network which will provide users with assured quality of service and the ability to seamlessly roam between buildings.
We use controllerless Aerohive access points in all our buildings. These are dual radio devices, operating on the 802.11ac wireless standard to provide the best current performance and future compatibility.
In addition to networking services we also provide a ‘follow-me’ print service, which is delivered as a managed service by Canon. Users are able to print from anywhere and then use their building pass to collect their prints from the nearest convenient printer.
WAN and PSN
Our ‘always on VPN’ approach allowed us a great deal of flexibility for Wide Area Network (WAN) circuits into buildings. Since the encryption is built in to the client device we didn’t need to buy expensive encrypted circuits and were able to procure a commodity WAN service.
Large building are supplied with circuits from Level 3. These are private VPLS circuits connecting the buildings to our IaaS data centres. Smaller buildings use either small private Level 3 circuits or public Internet circuits for connectivity.
We use Public Services Network (PSN) circuits from our data centres only for publishing or consuming services from other government departments and suppliers. This allows us to access shared services like our HR system from Shared Services, or for us to publish something like our Intranet.
The experience for users is seamless and identical regardless of where they are working. If they are in a Cabinet Office building they will benefit from the speed and reliability of our network, but the method for connecting is just the same if they happen to be at home or in a coffee shop.
We’ve already received a lot of feedback on how this architecture is positively affecting the way people can work. Beyond that, though, it’s allowing us to rapidly adapt and improve the service. The modular design allows us to swap out components and try new things. Even though we only just finished rollout out the service we are already starting to implement new products - and I hope that we never stop!
Don’t forget to sign up for email alerts for the Cabinet Office technology blog.

14 comments
Comment by Rob Knight posted on
Hi,
The End User Device guidance recommendation is a Foundation Grade assured VPN which from 2015 should use IKEv2 and yet Cabinet Office, who together with CESG produced the guidance, have elected to use a non-assured VPN client which only currently supports IKEv1?
As you'll be aware, IKEv1 is less tolerant of the two and doesn't support mobility in the way IKEv2 can.
Surely a Foundation Grade product such as Cisco AnyConnect, Microsoft IKEv2 or DirectAccess would have been better choices which at least meet the assurance recommendations you yourselves have made for operating at Official?!
Comment by Dave Holloway posted on
Thanks for the question, Rob. It raises one of the challenges we had with selecting products.
As mentioned in the post, our architecture is built around an 'always on' VPN for all devices. We wanted a product that was cross platform (Windows, OSX, IOS and Android), one where we could enforce the VPN connectivity and most importantly something that didn't require any action from users.
We considered VPN products from a number of vendors and the Palo Alto Global Protect product best met all of those requirements. Our default position on security products is to look for those with CPA Foundation Grade, but critically not at the cost of the user needs (unless absolutely necessary). Our security team agreed that if we could support this choice with sufficient assurance on the Palo Alto then it would be a viable option – to this end we worked closely with the vendor to assess their product against the relevant CPA Security Characteristics, taking into account Paolo Alto’s roadmap and CPA plans. Ultimately it's the product we felt provided the best user experience and with some careful due diligence we're confident of its suitability for use at OFFICIAL.
More generally, we feel that this approach demonstrates the real value of CPA – CESG did not establish the scheme to be used as a tick box or encourage unthinking procurements but instead to inform and support government’s security decision-making. On this basis it was invaluable to us.
Comment by Rob Knight posted on
Hi Dave,
Thanks for the reply and points you considered during your selection process.
Does the always on VPN affect the ability to use challenged Internet - I.e. Hotel Wi-Fi, business continuity using serviced offices etc?
Regards,
Rob Knight.
Comment by Steve Piggott posted on
Hi Dave,
How have you worked with Google to address the issues with Geograpically Dispersed Data faced when hosting OFFICIAL information in the Cloud?
Do Google offer a geo lock to Dublin for their service?
Steve Piggott
Comment by Tom Read posted on
Dear Dave,
We worked closely with Google to understand how user data is stored and protected across locations. As far as we're aware, Google does not offer single location hosting for Google Apps for Work, but we were satisfied with the security controls in place.
Comment by Gareth Thomas posted on
Hi Dave,
With Cabinet Office using a cloud email service and dropping .gsi from their email address have you had any issue with email communications at OFFICIAL - SENSITIVE? If so how have you addressed this?
Many thanks
Gareth Thomas
Comment by Catriona McGrath posted on
Dear Gareth,
OFFICIAL SENSITIVE is a handling caveat within the OFFICIAL security classification so doesn't require any special technical changes. We worked with other departments to ensure they were still able to email us without a .gsi in our email address.
Comment by Ola Alilaj posted on
Hi Dave,
Just curious if you are using Chrome Devices for your users, or simply the Chrome Browser is installed on any device, and whether you are using Google Cloud Print over wi-fi?
Thanks
Comment by Steve Allison posted on
For securing in-transit mobile data, are you making use of a private APN in addition to the always-on VPN?
Comment by Gregory Bennett posted on
Dear Steve,
Thanks for your question. We do not use a private APN.
Comment by Gregory Bennett posted on
Hi Rob. Yes, we can used challenged internet.
Comment by Ross Wheatley posted on
Dear Ola,
Thanks for your question. Chrome devices are not being used at present within the Cabinet Office for our end users. Nor are we implementing Google Cloud Print Over Wifi as it does not offer a guaranteed level of service. We have implemented a managed print service instead.
Comment by Jose posted on
Hi Dave,
Is there any reason why your users don't have Linux on their devices? Isn't that provided as an option?
Comment by Catriona McGrath posted on
Dear Jose,
Linux was considered as a possibly offering, however following the user needs' evaluations, there did not appear to be any demand for another Operating System on top of Windows and Mac OS. If the user needs change in the future, introducing a Linux Operating System could be possible as the majority of the solutions are completely platform independent.